Deleted Text Messages I often get asked about deleted text messages on...Read More
Our computer forensic team specializes in investigative techniques to identify, collect, analyze and present digital evidence in a manner that can be used in a court of law or other legal proceedings. We can uncover hidden information stored on computers and other devices, such as cloud accounts, social media, removable media, tablets or even audio/video recorders.


Hardware


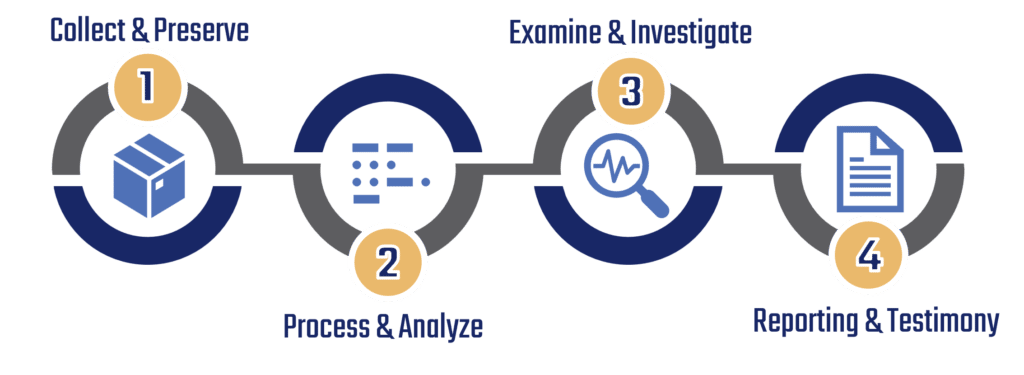
WORKFLOW
After an initial case review and client meeting, our experts will guide each client through the workflow process and determine which steps are appropriate for each specific case. Though we encourage our clients to utilize all four steps, all steps may not be necessary as our experts will assess client goals and desired outcomes before initiating forensic services.




FREQUENTLY ASKED QUESTIONS
Whether you’re curious about pricing, features, or how to get started, you’ll find helpful information that can guide you.

What is the process of transferring your data or device(s)?
We can accept / collect data or devices in a variety of ways. After an initial consultation, our team will determine the most cost effective option for your specific needs.



How long can I expect the process to take?
Your case may not require us to utilize each step; a timeline for your case will be determined after an initial assessment by our forensic team. Initial assessments can take up to 24-72 hours.
Can I get more information than just the data?
Our workflow process consists of four steps:

You are welcome to use as many steps as you’d like; or team of experts can also walk you through which steps are most appropriate for your needs.
Does the device have to be unlocked?
It is recommended that you unlock and unencrypt any device(s) that are provided to our team of experts. If you do not feel comfortable performing this step, please provide us with the information or credentials we would need to perform this for you.

If you are unable to provide us with credentials to unlock or decrypt your device(s), our experts do have access to advanced tools that can help. Contact us for further details regarding this specialized service.
Do you store the data from my device after it is sent back to me?
During our workflow process, device data is stored in a secure location; retention periods for data storage varies on a case-by-case basis.

Once we have completed our workflow, data will either be destroyed or returned based on the contract requirements agreed to.
Will you send me back reports and files I can easily read?
Our extraction software systems for most of our services includes a reader-friendly conversion tool, typically in PDF format. However, if you need the proprietary data as well, we can assist you by sending a freeware link along with the data file to access the information.
INSIGHTS
Get expert insights from seasoned forensic professionals to strengthen your defense and uncover critical evidence.
Deleted Text Messages I often get asked about deleted text messages on...Read More
In an increasingly digitized world, data has become a vital source of...Read More
In today’s digital age, applications (apps) have become an integral part of...Read More
In the digital age, social media platforms have become an integral part...Read More
By subscribing you agree with our Privacy Policy and provide consent to receive updates from our company.