Need Help?
If you can’t find what you need from the resources below, feel free to reach out and contact us directly.
Frequently Asked Questions
We can accept / collect data or devices in a variety of ways. After an initial consultation, our team will determine the most cost effective option for your specific needs.



Our workflow process consists of four steps:
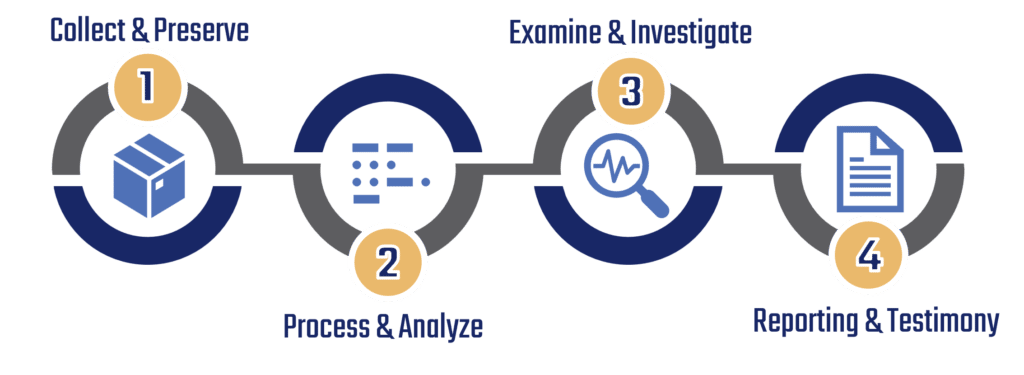
Your case may not require us to utilize each step; a timeline for your case will be determined after an initial assessment by our forensic team. Initial assessments can take up to 24-72 hours.
Our workflow process consists of four steps:

You are welcome to use as many steps as you’d like; or team of experts can also walk you through which steps are most appropriate for your needs.
It is recommended that you unlock and unencrypt any device(s) that are provided to our team of experts. If you do not feel comfortable performing this step, please provide us with the information or credentials we would need to perform this for you.

If you are unable to provide us with credentials to unlock or decrypt your device(s), our experts do have access to advanced tools that can help. Contact us for further details regarding this specialized service.
During our workflow process, device data is stored in a secure location; retention periods for data storage varies on a case-by-case basis.

Once we have completed our workflow, data will either be destroyed or returned based on the contract requirements agreed to.
Our extraction software systems for most of our services includes a reader-friendly conversion tool, typically in PDF format. However, if you need the proprietary data as well, we can assist you by sending a freeware link along with the data file to access the information.
Knowledge Exchange

Deleted Text Messages
Deleted Text Messages I often get asked about deleted text messages on cellular devices, specifically SMS or MMS messages on cellular devices. Can I recover



