Our Story

Our Mission
Services
Collect usage, history, and data from personal computers. We use the latest technology to gather all the data without missing a byte and provide you with an easy-to-understand analysis report so you have all the information you need to help you solve your case.
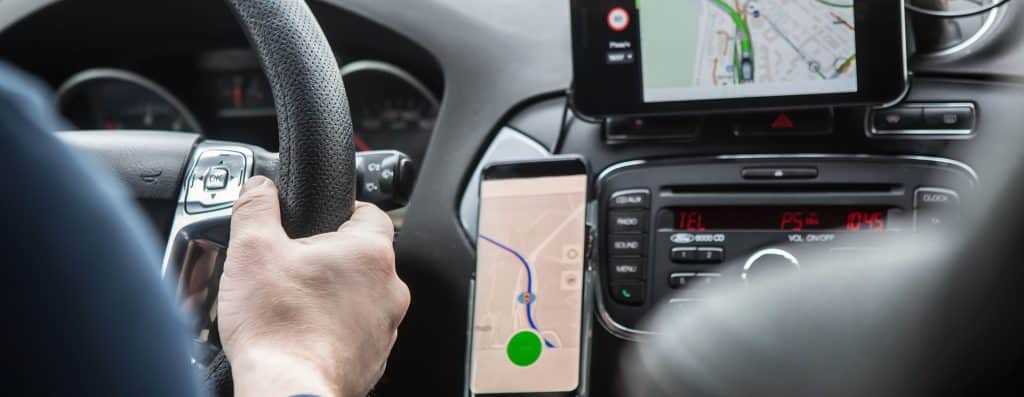
Vehicles contain a massive amount of information helpful in an investigation, including connected devices and location data. Using industry-leading tools, we acquire vehicle usage and history data to help you understand what happened when the incident happened, and who was involved.
Mobile devices are a major source of digital evidence in today’s investigations. We extract complete forensic images of mobile devices without any data contamination or loss, analyze the information, and send you an easy-to-review report of our findings.
TRAININGS
Receive expert training for all experience levels. With decades of combined experience in law enforcement and analysis, our training team teaches you how to use digital forensics tools to their fullest extent, so you can be confident you have the skills to effectively conduct your investigation.
DFC101 – DATA STORAGE AND ENCRYPTION
This four-hour course will go through three modules on the basics of Data Storage and Encryption. Some of those topics include Understanding Raw Data, Storage Media and Hashing. This course will conclude with an exam at the end to certify your training.
In addition to providing data extraction and analyzation as a service, Defense Forensic wants to educate members of our community on digital forensics. While the world of technology changes, we are here to inform this community on how a digital footprint can be traced.
There is a lack of knowledge on what data can be pulled from mobile devices, computers, and vehicles. Our analysts take these devices and run our software through them to pull every bit of information out of them. If needed, our team can analyze the data itself to give our clients the best understanding of what the data is telling us.
This four-hour course will go through three modules on the basics of Data Storage and Encryption. Some of those topics include Understanding Raw Data, Storage Media and Hashing. This course will conclude with an exam at the end to certify your training.
In addition to providing data extraction and analyzation as a service, Defense Forensic wants to educate members of our community on digital forensics. While the world of technology changes, we are here to inform this community on how a digital footprint can be traced.
There is a lack of knowledge on what data can be pulled from mobile devices, computers, and vehicles. Our analysts take these devices and run our software through them to pull every bit of information out of them. If needed, our team can analyze the data itself to give our clients the best understanding of what the data is telling us.
“This one-day self-paced course is designed to provide legal professionals and examiners a basic understanding of how to navigate the engagement process of a digital forensic investigation, understand the capabilities and limitations of a digital forensic examiner, select a digital forensic examiner, and even perform basic digital forensic investigations in-house.”
$295 per class registration
Register for Forensic Training
*Payment will be taken once a Defense Forensic team member reaches out confirming your registration

FAQ's
- You will be sent a shipping label to attach to your package
- Once received you will get notified that the forensic examination has begun
- Once the device is shipped back to you, you will be notified via email
- 24-72 hours dependent on shipping
- Priority projects can be paid for
- Unlocked device extractions typically include any multimedia stored on the device, such as photos and videos, as well as application information and usage, communications, and browser history, among many other data points.
- Yes, we can analyze device data after it is acquired to provide additional findings if necessary.
- In most cases, yes. If you have a device that is locked, please contact us for further information.
- Device data is stored in a secure location, though retention periods may vary. Please contact us for additional information regarding long-term data retention.
- As many as you’d like
- Yes, storage removal varies from device to device, but we can walk you through the removal process if necessary.
- Our forensic tools are regularly tested and validated by our team to ensure that acquired data is true and accurate to the raw device data.
- Feel free to contact us at info@defenseforensic.com and we will work with you on any questions you have
LET US HELP YOU FIND THE TRUTH IN DATA.
- 923 S. Hastings Way #201 Eau Claire WI 54703
- Info@DefenseForensic.com
- (888) 282-2379

